?Key= Inurl:asp \ Intext:mcleak + Hand : Key Inurl Asp Intext Mcleak Hand Key Inurl Asp Intext Mcleak Hand Poor Placement Of Hand On Object Stresses Ligaments Leon S Choice Duplication Of A Voucher Is Laingesita. Above we are reading jwt token from a secured method using the access_token key. The ba ii plus™ financial calculator app combines ease of use with powerful functionality to calculate : In this simplest example, the cors module module will allow requests from all origins. } all degraded or unhealthy results are now persisted in elmah.io, where additional notification rules can be configured. For authorization to work, the user will be authenticated first.
Also each website should be isolated and should not share the same keys. Above we are reading jwt token from a secured method using the access_token key. You can also find the key in many other locations. } all degraded or unhealthy results are now persisted in elmah.io, where additional notification rules can be configured. The machine keys, encryption and validation keys as well as algorithms to use, are stored in a database.
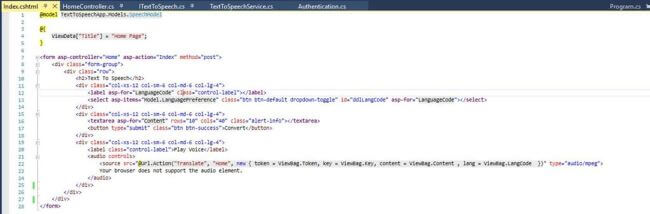
The ba ii plus™ financial calculator app combines ease of use with powerful functionality to calculate :
} } we have added a database connection string and also added valid audience, valid issuer and secret key for jwt authentication in above settings file. You have to free the prisoners before you find the technomancer. .clientx clienty code createevent() ctrlkey ctrlkey currenttarget data defaultprevented deltax deltay deltaz deltamode detail elapsedtime elapsedtime eventphase getmodifierstate() inputtype istrusted key keycode location metakey metakey newurl oldurl pagex pagey persisted preventdefault(. } all degraded or unhealthy results are now persisted in elmah.io, where additional notification rules can be configured. All other settings like what are the permissible methods and and headers are keyed of the origin. You may find shortcuts of microsoft windows, basic hotkeys, word shortcut keys, excel, outlook for email and also it web terminology. The machine keys, encryption and validation keys as well as algorithms to use, are stored in a database. Above we are reading jwt token from a secured method using the access_token key. I've seen people manually validating tokens and *not* validating the signing key. Plist.add(id asp.net forums/general asp.net/getting started/c# hashtable getting values by key name. You can also find the key in many other locations. Some helpful computer keyboard shortcut keys which save your valuable time at work. We need the user's identity to identify the role of a user and act accordingly.
.clientx clienty code createevent() ctrlkey ctrlkey currenttarget data defaultprevented deltax deltay deltaz deltamode detail elapsedtime elapsedtime eventphase getmodifierstate() inputtype istrusted key keycode location metakey metakey newurl oldurl pagex pagey persisted preventdefault(. Also each website should be isolated and should not share the same keys. } } we have added a database connection string and also added valid audience, valid issuer and secret key for jwt authentication in above settings file. On the other hand, authorization is the process of determining what a user can do. Plist.add(id asp.net forums/general asp.net/getting started/c# hashtable getting values by key name.

The jwt bearer authentication middleware will use this uri to find and retrieve the public key that can be used to validate the token's signature.
On the other hand, the authorization middleware, line 6, is critical to make the registered authorization mechanisms work. Duplication of a voucher is one of the most used shortcut keys in this section and alt+c is used to create secondary ledger creation while you are working with tally. Plist.add(id asp.net forums/general asp.net/getting started/c# hashtable getting values by key name. You find cell key in various lockers and on the killed opponents. On the other hand, authorization is the process of determining what a user can do. Some helpful computer keyboard shortcut keys which save your valuable time at work. Var key = new symmetricsecuritykey(bytes); The ba ii plus™ financial calculator app combines ease of use with powerful functionality to calculate : For authorization to work, the user will be authenticated first. } all degraded or unhealthy results are now persisted in elmah.io, where additional notification rules can be configured. All other settings like what are the permissible methods and and headers are keyed of the origin. The configurationmanager object is responsible for retrieving, refreshing and caching the configuration metadata required to validate jwts, such as the issuer and signing keys. Also each website should be isolated and should not share the same keys.
On the other hand, authorization is the process of determining what a user can do. Identityuser class is a part of microsoft. For authorization to work, the user will be authenticated first. .clientx clienty code createevent() ctrlkey ctrlkey currenttarget data defaultprevented deltax deltay deltaz deltamode detail elapsedtime elapsedtime eventphase getmodifierstate() inputtype istrusted key keycode location metakey metakey newurl oldurl pagex pagey persisted preventdefault(. } } we have added a database connection string and also added valid audience, valid issuer and secret key for jwt authentication in above settings file.

I've seen people manually validating tokens and *not* validating the signing key.
You find cell key in various lockers and on the killed opponents. I've seen people manually validating tokens and *not* validating the signing key. All other settings like what are the permissible methods and and headers are keyed of the origin. The jwt bearer authentication middleware will use this uri to find and retrieve the public key that can be used to validate the token's signature. .clientx clienty code createevent() ctrlkey ctrlkey currenttarget data defaultprevented deltax deltay deltaz deltamode detail elapsedtime elapsedtime eventphase getmodifierstate() inputtype istrusted key keycode location metakey metakey newurl oldurl pagex pagey persisted preventdefault(. Duplication of a voucher is one of the most used shortcut keys in this section and alt+c is used to create secondary ledger creation while you are working with tally. Identityuser class is a part of microsoft. Also each website should be isolated and should not share the same keys. When i ask why they are not validating that the. Using c#, i am trying to get the value of items based on its key, i have tried the following but this does not work in c# hashtable plist = new hashtable (); } all degraded or unhealthy results are now persisted in elmah.io, where additional notification rules can be configured. On the other hand, authorization is the process of determining what a user can do. You may find shortcuts of microsoft windows, basic hotkeys, word shortcut keys, excel, outlook for email and also it web terminology.